如何加载Ext4文件系统
2024.05.10
此文感谢 建军,UEFI Shell下,可以不用复制编译好的独立 .efi到Fat32 U盘加载了,直接从Ext4 Linux文件系统加载。
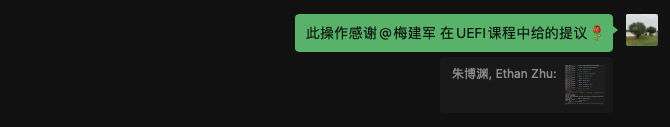
如下面重新排序后的BLK0-BLK7, BLK1和BLK4的文件系统被识别加载(FAT32),BLK2为Linux Ext4分区,没有被识别和加载。
UEFI v2.70 (EDK II, 0x00010000)
Mapping table
BLK0: Alias(s): PcieRoot(0x0)/Pci(0x0,0x0)/Pci(0x0,0x0)/NVMe(0x1,32-03-00-00-00-00-00-00)
FS0: Alias(s):HD0b:;BLK1: PcieRoot(0x0)/Pci(0x0,0x0)/Pci(0x0,0x0)/NVMe(0x1,32-03-00-00-00-00-00-00)/HD(1,GPT,9DD431F3-1E15-584E-987D-827DD40C2E49,0xF000,0x200000)
BLK2: Alias(s): PcieRoot(0x0)/Pci(0x0,0x0)/Pci(0x0,0x0)/NVMe(0x1,32-03-00-00-00-00-00-00)/HD(2,GPT,8DEE4DA3-BB01-D348-8C62-188B9C031AC1,0x20F000,0x389AB019)
BLK3: Alias(s): VenHw(100C2CFA-B586-4198-9B4C-1683D195B1DA)
FS1: Alias(s):HD1b:;BLK4: VenHw(100C2CFA-B586-4198-9B4C-1683D195B1DA)/HD(1,GPT,809A75D3-E97F-4F9F-9E15-C4EB053E8AB3,0x800,0x32000)
BLK5: Alias(s): VenHw(100C2CFA-B586-4198-9B4C-1683D195B1DA)/HD(2,GPT,836136C3-A854-4F12-8FCD-3F5BCE5C9F24,0x32800,0x8000)
BLK6: Alias(s): VenHw(100C2CFA-B586-4198-9B4C-1683D195B1DA)/HD(3,GPT,8B6032D1-3641-44F6-B489-C48D195AC17E,0x3A800,0xE543000)
BLK7: Alias(s): VenHw(100C2CFA-B586-4198-9B4C-1683D195B1DA)/HD(4,GPT,96CA6224-A52D-4641-A947-AA3CCBA8DC8C,0xE57D800,0xFA000)尝试打开blk2失败: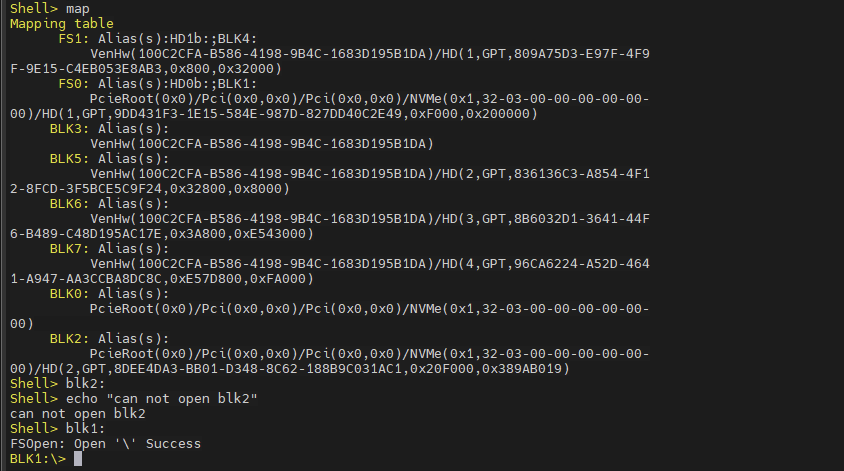
可以将Ext4Dxe.efi 复制到Fat32格式的U盘,在UEFI Shell下从U盘加载;
此时,在UEFI Shell下可从U盘将Ext4Dxe.efi复制到BLK1下,以后就不用U盘了。(没有U盘,可以在Linux下挂载引导分区,然后将Ext4Dxe.efi复制进去)
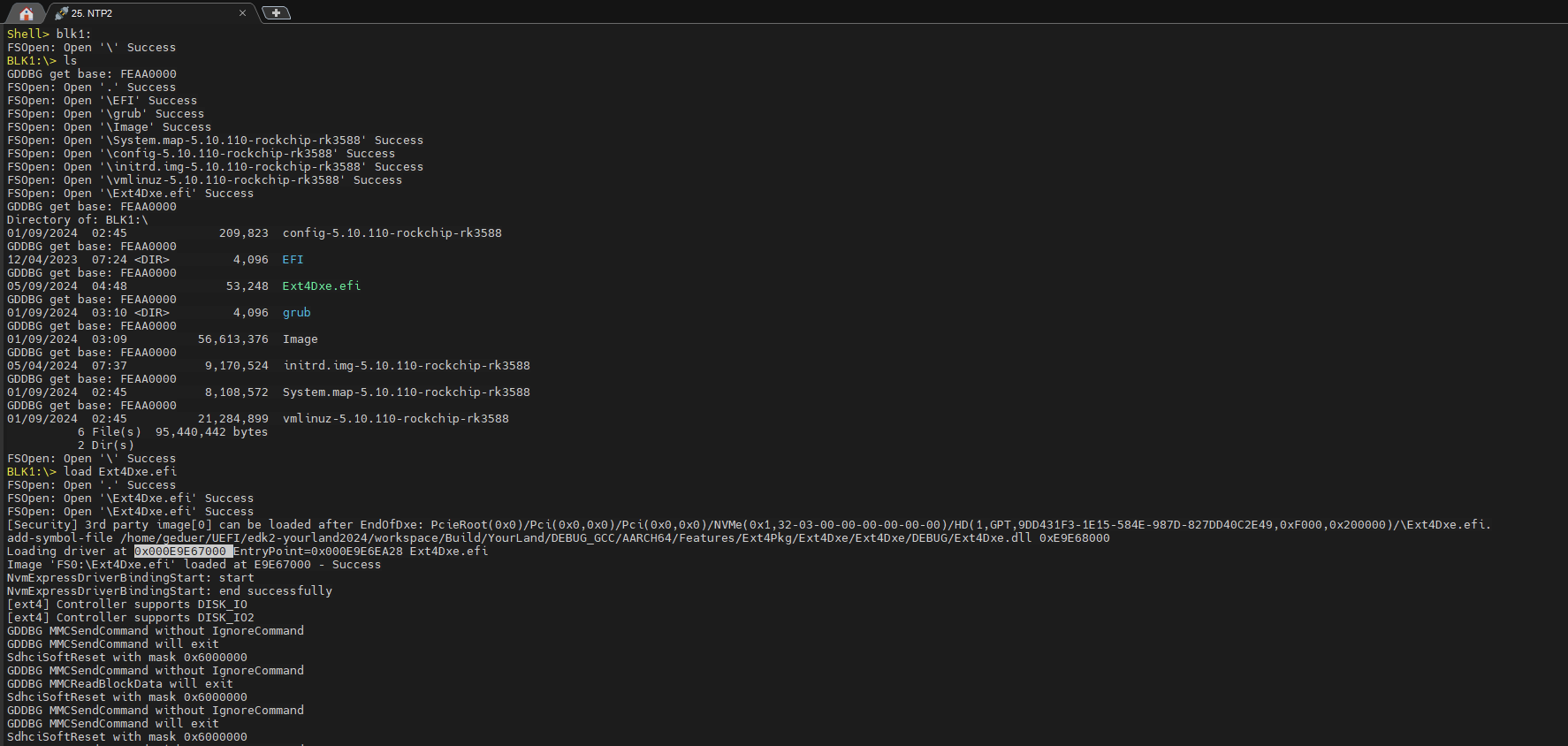
这样就可以访问BLK2了: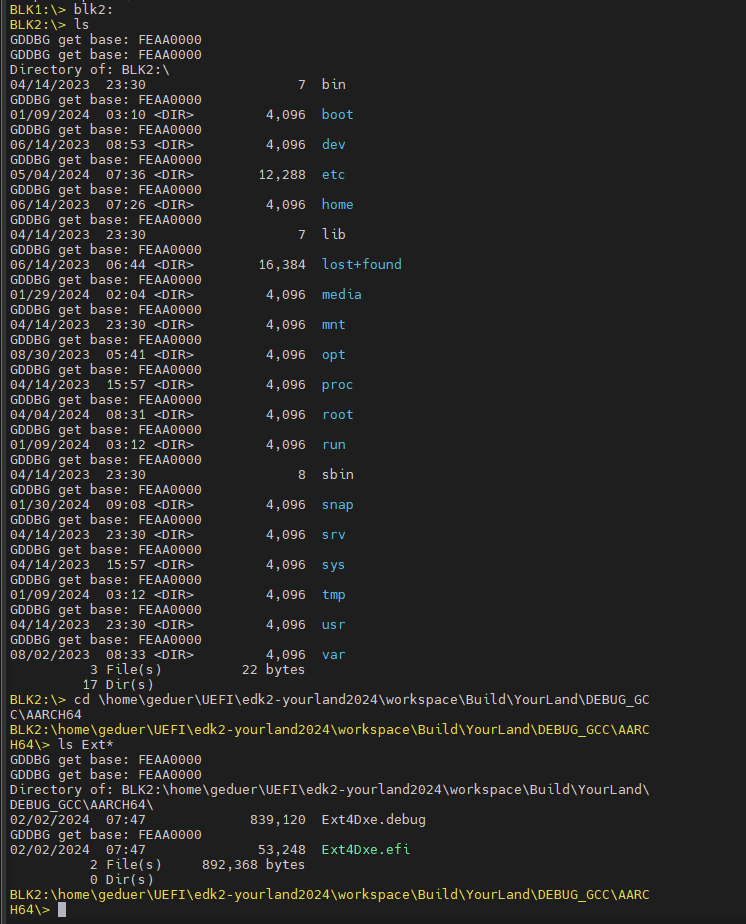
此时,BLK2可以访问,但map命令显示没有别名: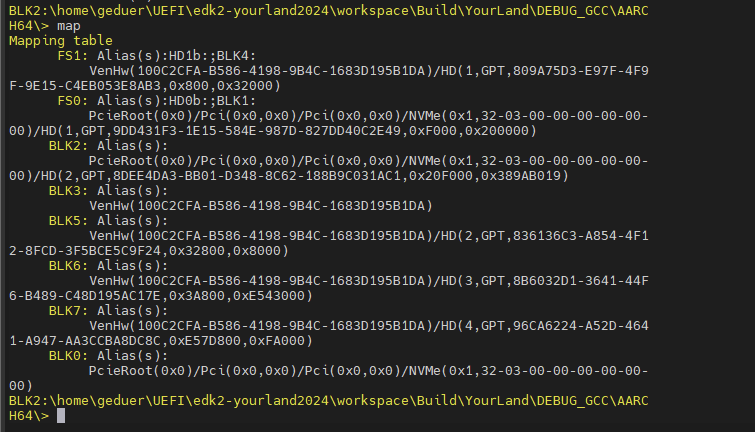
可退出Shell再重新进入,就有了: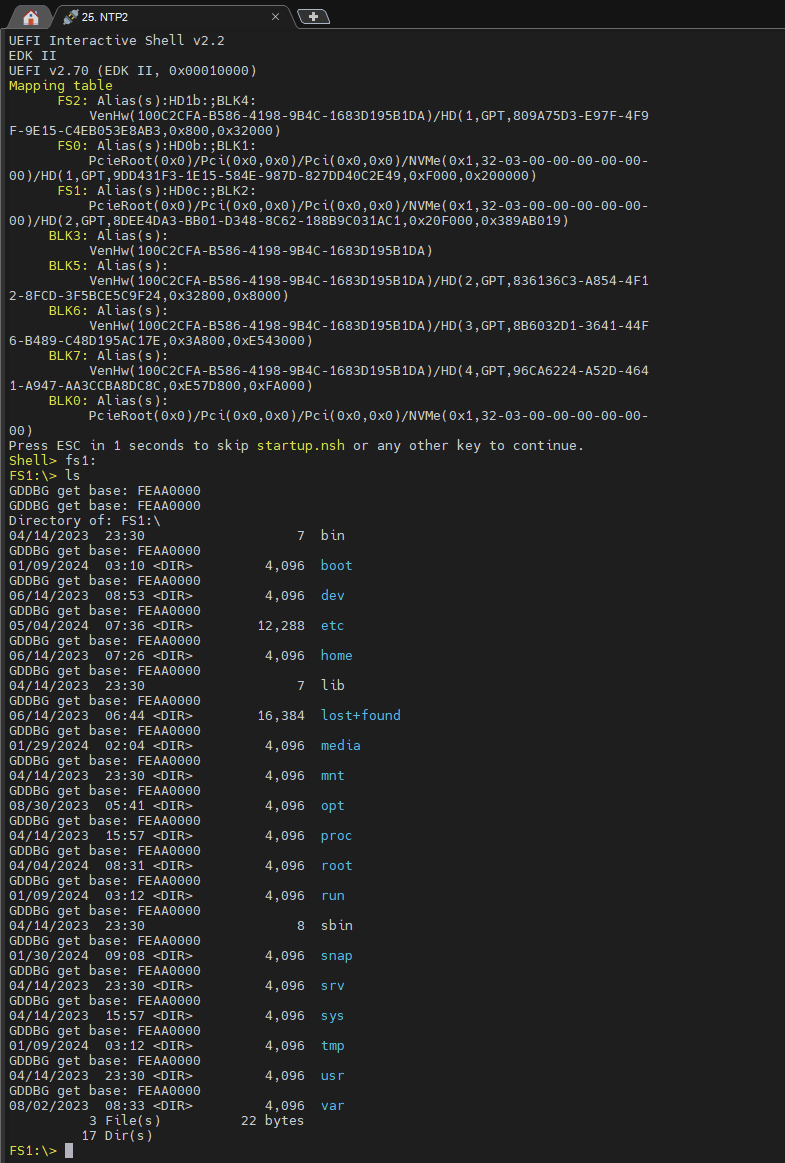
想要调试观察学习Ext4Dxe,可以在NDB中手动加载其符号:
BLK1:> load Ext4Dxe.efi
FSOpen: Open ‘.’ Success
FSOpen: Open ‘\Ext4Dxe.efi’ Success
FSOpen: Open ‘\Ext4Dxe.efi’ Success
[Security] 3rd party image[0] can be loaded after EndOfDxe: PcieRoot(0x0)/Pci(0x0,0x0)/Pci(0x0,0x0)/NVMe(0x1,32-03-00-00-00-00-00-00)/HD(1,GPT,9DD431F3-1E15-584E-987D-827DD40C2E49,0xF000,0x200000)/\Ext4Dxe.efi.
add-symbol-file /home/geduer/UEFI/edk2-yourland2024/workspace/Build/YourLand/DEBUG_GCC/AARCH64/Features/Ext4Pkg/Ext4Dxe/Ext4Dxe/DEBUG/Ext4Dxe.dll 0xE9E68000
Loading driver at 0x000E9E67000 EntryPoint=0x000E9E6EA28 Ext4Dxe.efi
05/09/2024 04:48 53,248 Ext4Dxe.efi
交叉校验,并加载,再校验: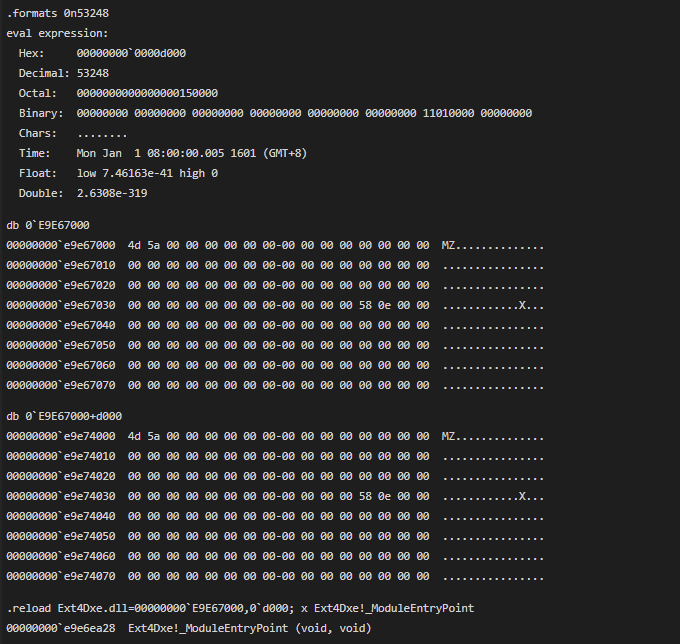
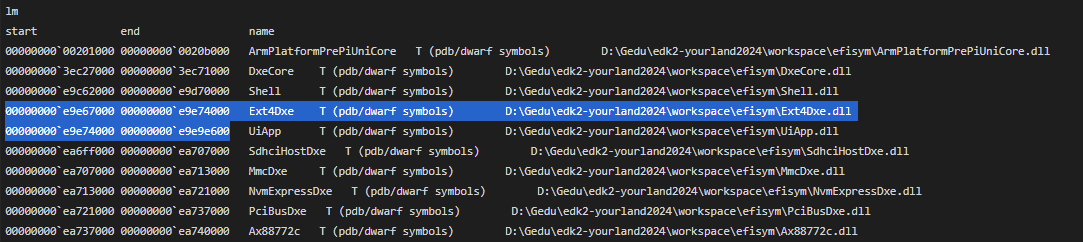
.formats 0n53248
eval expression:
Hex: 00000000`0000d000
Decimal: 53248
Octal: 0000000000000000150000
Binary: 00000000 00000000 00000000 00000000 00000000 00000000 11010000 00000000
Chars: ........
Time: Mon Jan 1 08:00:00.005 1601 (GMT+8)
Float: low 7.46163e-41 high 0
Double: 2.6308e-319
db 0`E9E67000
00000000`e9e67000 4d 5a 00 00 00 00 00 00-00 00 00 00 00 00 00 00 MZ..............
00000000`e9e67010 00 00 00 00 00 00 00 00-00 00 00 00 00 00 00 00 ................
00000000`e9e67020 00 00 00 00 00 00 00 00-00 00 00 00 00 00 00 00 ................
00000000`e9e67030 00 00 00 00 00 00 00 00-00 00 00 00 58 0e 00 00 ............X...
00000000`e9e67040 00 00 00 00 00 00 00 00-00 00 00 00 00 00 00 00 ................
00000000`e9e67050 00 00 00 00 00 00 00 00-00 00 00 00 00 00 00 00 ................
00000000`e9e67060 00 00 00 00 00 00 00 00-00 00 00 00 00 00 00 00 ................
00000000`e9e67070 00 00 00 00 00 00 00 00-00 00 00 00 00 00 00 00 ................
db 0`E9E67000+d000
00000000`e9e74000 4d 5a 00 00 00 00 00 00-00 00 00 00 00 00 00 00 MZ..............
00000000`e9e74010 00 00 00 00 00 00 00 00-00 00 00 00 00 00 00 00 ................
00000000`e9e74020 00 00 00 00 00 00 00 00-00 00 00 00 00 00 00 00 ................
00000000`e9e74030 00 00 00 00 00 00 00 00-00 00 00 00 58 0e 00 00 ............X...
00000000`e9e74040 00 00 00 00 00 00 00 00-00 00 00 00 00 00 00 00 ................
00000000`e9e74050 00 00 00 00 00 00 00 00-00 00 00 00 00 00 00 00 ................
00000000`e9e74060 00 00 00 00 00 00 00 00-00 00 00 00 00 00 00 00 ................
00000000`e9e74070 00 00 00 00 00 00 00 00-00 00 00 00 00 00 00 00 ................
.reload Ext4Dxe.dll=00000000`E9E67000,0`d000; x Ext4Dxe!_ModuleEntryPoint
00000000`e9e6ea28 Ext4Dxe!_ModuleEntryPoint (void, void)
lm
start end name
00000000`00201000 00000000`0020b000 ArmPlatformPrePiUniCore T (pdb/dwarf symbols) D:\Gedu\edk2-yourland2024\workspace\efisym\ArmPlatformPrePiUniCore.dll
00000000`3ec27000 00000000`3ec71000 DxeCore T (pdb/dwarf symbols) D:\Gedu\edk2-yourland2024\workspace\efisym\DxeCore.dll
00000000`e9c62000 00000000`e9d70000 Shell T (pdb/dwarf symbols) D:\Gedu\edk2-yourland2024\workspace\efisym\Shell.dll
00000000`e9e67000 00000000`e9e74000 Ext4Dxe T (pdb/dwarf symbols) D:\Gedu\edk2-yourland2024\workspace\efisym\Ext4Dxe.dll
00000000`e9e74000 00000000`e9e9e600 UiApp T (pdb/dwarf symbols) D:\Gedu\edk2-yourland2024\workspace\efisym\UiApp.dll
00000000`ea6ff000 00000000`ea707000 SdhciHostDxe T (pdb/dwarf symbols) D:\Gedu\edk2-yourland2024\workspace\efisym\SdhciHostDxe.dll
00000000`ea707000 00000000`ea713000 MmcDxe T (pdb/dwarf symbols) D:\Gedu\edk2-yourland2024\workspace\efisym\MmcDxe.dll
00000000`ea713000 00000000`ea721000 NvmExpressDxe T (pdb/dwarf symbols) D:\Gedu\edk2-yourland2024\workspace\efisym\NvmExpressDxe.dll
00000000`ea721000 00000000`ea737000 PciBusDxe T (pdb/dwarf symbols) D:\Gedu\edk2-yourland2024\workspace\efisym\PciBusDxe.dll
00000000`ea737000 00000000`ea740000 Ax88772c T (pdb/dwarf symbols) D:\Gedu\edk2-yourland2024\workspace\efisym\Ax88772c.dll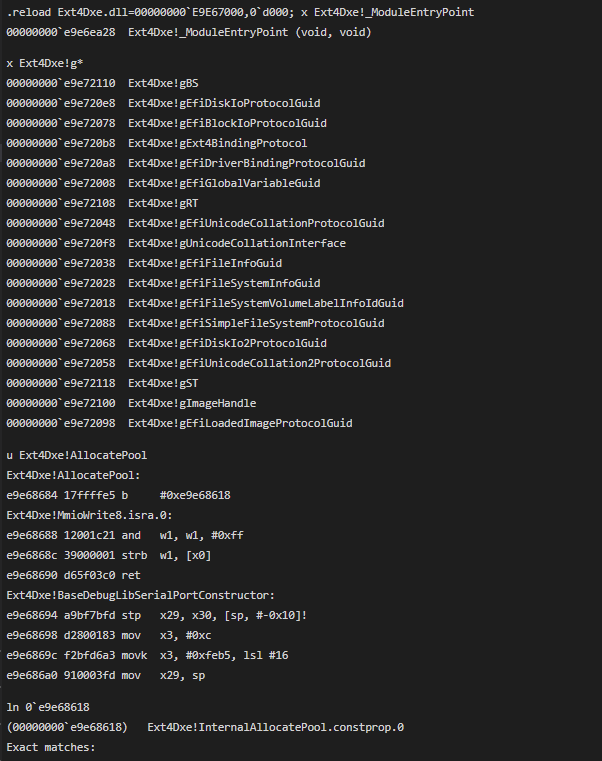

这些已编译的Modules是没有写入UEFI FV的,包括Ext4Dxe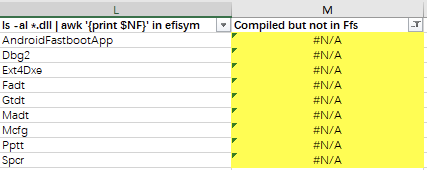
最后编辑:朱博渊 更新时间:2025-04-21 15:23
